
CrowdStrike Falcon Identity Threat Protection
Prevent breaches with frictionless risk-based authentication
Falcon Identity Threat Protection
CrowdStrike Falcon Identity Threat Protection enables hyper accurate threat detection and real-time prevention of identity-based attacks combining the power of advanced AI, behavioral analytics and a flexible policy engine to enforce risk-based conditional access.
Multi-Directory Identity Protection Across On-Premises and Clouds
CrowdStrike Falcon Identity Threat Protection, a part of the CrowdStrike Falcon Platform, enables frictionless security with real-time threat prevention and IT policy enforcement using identity, behavioral and risk analytics. A full 80% of breaches involve compromised credentials, and therefore segmenting identities, automating enforcement and using risk-based conditional access to verify authentication traffic can reduce risk and reduce IT complexity.
Key Benefits of Choosing Identity Threat Protection
Frictionless Realtime Protection From Identity-Based Threats

GAIN VISIBILITY OF WORKFORCE IDENTITIES ACROSS MULTI-DIRECTORY ENVIRONMENTS
Falcon Identity Threat Protection enables unified visibility and control of user access to applications, resources and identity stores, with actionable insights into user behavior and risks, eliminating security blindspots across hybrid environments.

GET HYPER-ACCURATE THREAT DETECTION AND REDUCE RESPONSE TIMES DRAMATICALLY
Falcon Identity Threat Protection reduces false positives, brings down the mean time to detect and resolve incidents by eliminating the need for complex, error-prone log analysis, and improves SOC analysts’ efficiencies by cutting down alert fatigue.

ENABLE REAL-TIME PREVENTION OF IDENTITY-BASED ATTACKS WITH CONDITIONAL ACCESS POLICIES
Falcon Identity Threat Protection enforces consistent risk-based policies to automatically block, allow, audit or step up authentication for every identity, at the same time ensuring a frictionless login experience for genuine users.
Segment Workforce Identities
- Provides continuous multi-directory visibility into the scope and the impact of access privileges for identities across Microsoft Active Directory (AD), Azure AD and cloud single sign-on (SSO) solutions.
- Automatically classifies identities into hybrid (identities that are on on-premises and cloud AD) and cloud-only (identities that reside only on Azure AD).
- Segments accounts into human, service, shared accounts and privileged accounts.
- Provides a customizable attack surface overview with insights into user risk and behavior changes over time, like an increase in account lockouts, high-risk endpoints, compromised passwords, etc.
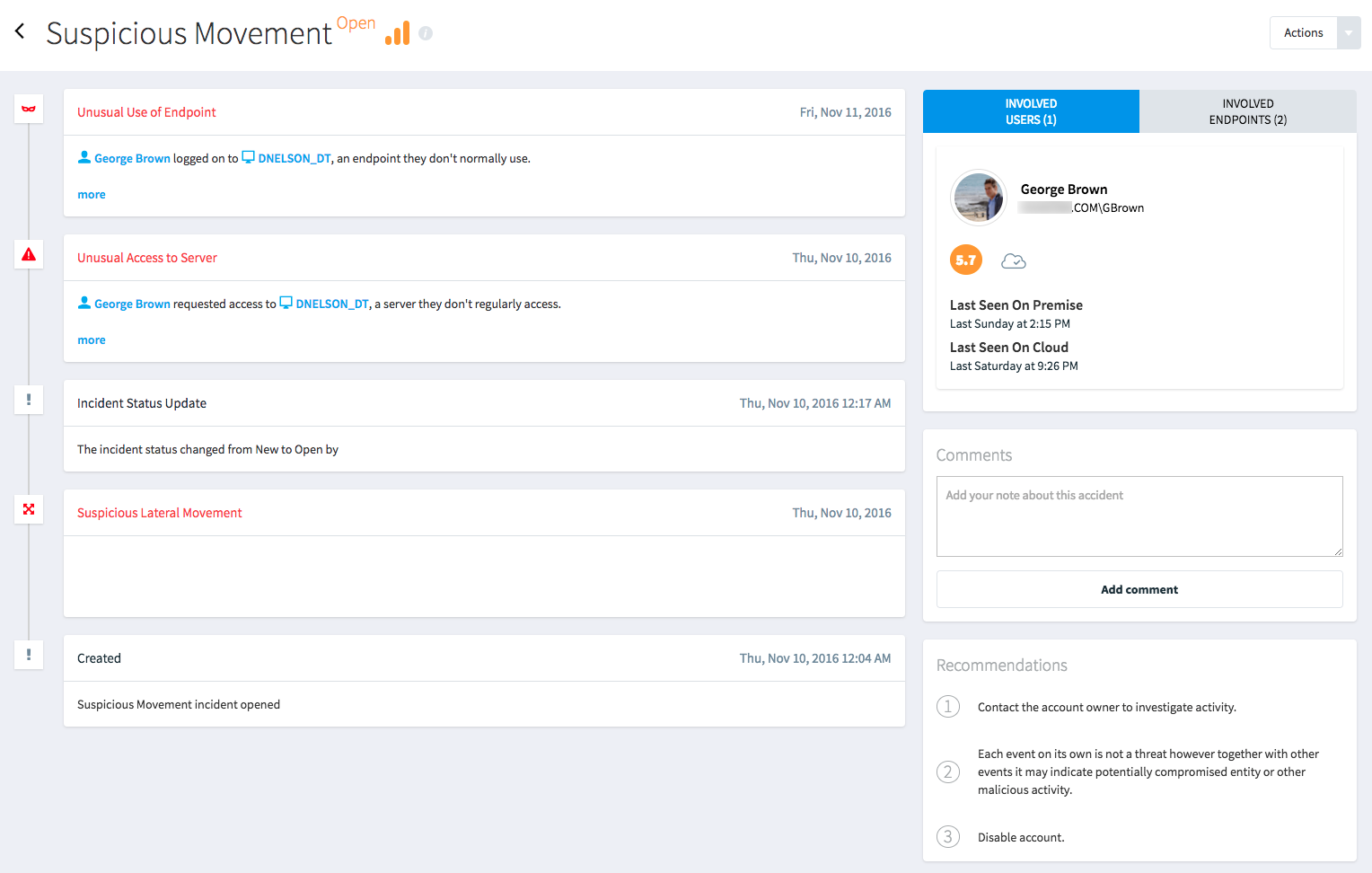

Automate Threat Detection and Response
- Enables hybrid identity store protection with continuous inspection of live authentication traffic, including encrypted protocols such as LDAP/S.
- Provides continuous assessment of security and incidents around identity threats without requiring the ingestion of logs or complex analysis.
- Uncovers reconnaissance (e.g., LDAP, BloodHound, SharpHound, credential compromise attacks), lateral movement (e.g., RDP, Mimikatz tool, unusual endpoint usage, unusual service logins, etc), and persistence (e.g., Golden Ticket attack) with advanced analytics and patented machine learning technology.
- Speeds up security investigations using intuitive threat hunting, with predefined search criteria, like but not limited to authentication events, unencrypted protocols, user roles, IP reputation and risk scores.
Verify Identities with Zero Friction
Falcon Identity Threat Detection maps against the MITRE ATT&CK framework to help you build a more complete security coverage. It offers detections for many sub-groups of these top-level techniques:
- Defines and enforces policies in real time, based on authentication patterns, behavior baselines and individual risk scores to verify identities using step-up authentication such as multifactor authentication (.e.g MFA).
- Automatically secures access to identity stores and applications, with improved user experience, by triggering identity verification only when the risk increases or if there’s a deviation from normal behavior.
- Reduces the attack surface by extending MFA to any resource or application, including legacy/proprietary systems and tools - for example, desktops that are not covered by cloud-based MFA solutions, and tools like PowerShell and protocols like RDP over NTLM.
- Automatically resolves security incidents that the user approves using identity verification methods such as 2FA/MFA, without involving security analysts and help desk tickets.
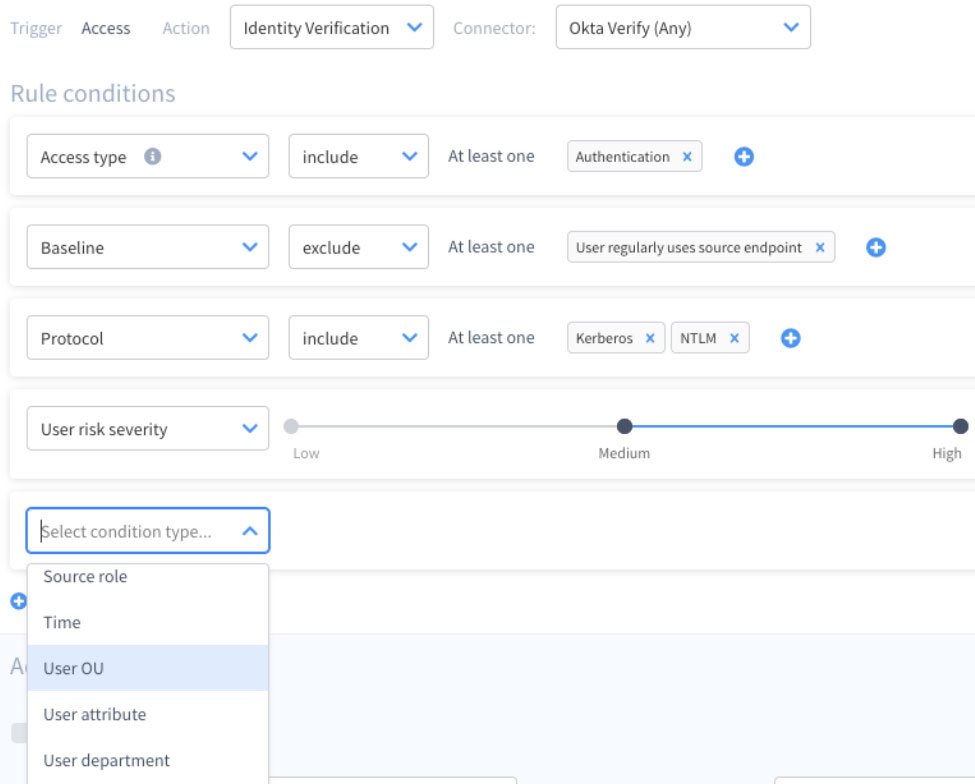
Key Capabilities
Segment
Gain granular and continuous insights into every account and activity to highlight identity security gaps across identity stores, and empower your identity and access management (IAM) and security teams to better evaluate identities and the risks associated with them.
- Continuous multi-directory visibility: Get deeper visibility into the scope and the impact of access privileges for identities across Microsoft Active Directory (AD) and Azure AD.
- Auto-classification of all accounts: Automatically classify identities into hybrid (identities that are on-premises and cloud AD) and cloud-only (identities that reside only on Azure AD), and segment accounts into human, service, shared accounts and privileged accounts.
- Customizable Active Directory security posture overview: Analyze user risk and behavior changes over time, like increase in account lockouts, high-risk endpoints and compromised passwords to get an overview of the attack surface of the organization.
Automate
Enable real-time identity threat detection and protection without time-consuming log processing. Eliminate risky guesswork and prioritize authentication tasks based on 100+ behavior analytics and risk factors for every account.
- Hybrid identity store protection: Continuously assess the directory configuration, like Group Policy Objects (GPO), LDAP configurations and risky protocols. Analyze every account from on-premises to hybrid identity stores. Inspect live authentication traffic, including encrypted protocols (e.g., LDAP/S).
- No-log, real-time threat detection: Continuously assess identity events and automatically associate them with threats and malicious intent, in real time, without ingesting logs with Falcon Identity Threat Protection's out-of-the-box machinelearning-powered detection rules. With advanced analytics and patented machine learning, uncover reconnaissance (e.g., LDAP, BloodHound, SharpHound, credential compromise attacks), lateral movement (e.g., RDP, pass-the-hash (PtH), Mimikatz tool, unusual endpoint usage, unusual service logins, etc.), and persistence (e.g., Golden Ticket attack, privilege escalation, etc.).
- Intuitive threat hunting: Investigate faster with unified domain access into detailed activities of every account across hybrid identity stores without the need for complex, string-based queries. Choose from a list of predefined search criteria, including authentication events, use of unencrypted protocols, user roles, IP reputation, risk scores and many more. If required, create and save your own search criteria to proactively sift through raw events and email them as periodic reports.
- Comprehensive API coverage: Extend the CrowdStrike Falcon platform's risk score and high-fidelity information to other apps (e.g., AD FS, SSO, IT systems and over 50+ integrations) with minimal effort using APIbased connectors.
Verify
Secure employee or contractor access to applications, tools and resources with a zero-friction user experience. Ensure consistent login experience for genuine users, but automatically step up authentication when risk scores increase.
- Zero-friction identity verification with flexible policies: Define and enforce access policies with simple rules with Falcon Identity Threat Protection adaptive analysis, eliminating the need to write complex static conditions for every user. The policies are based on authentication patterns, behavior baselines, individual user risk score and device risk score (via API integration) to verify identities using MFA. This robust methodology secures access to identity stores and applications, with improved user experience - i.e., identity verification is triggered only when the risk increases or if there’s a deviation from normal behavior.
- Improved security posture with extended MFA: Extend identity verification/MFA to any resource or application, including legacy/proprietary systems and tools that traditionally could not be integrated with MFA - for example, desktops that are not covered by cloud-based MFA solutions, and tools like PowerShell and protocols like RDP over NTLM - to reduce the attack surface.
- Auto-resolve security incidents: With the platform’s customizable enforcement policies, resolve standard incidents that the user approves using identity verification methods (2FA/MFA), so that your security analysts can focus on critical security incidents. Additionally, resolve these incidents with effortless API integrations into SOAR, SIEM and ticketing platforms.
Documentation:
Download the CrowdStrike Falcon Identity Threat Protection Datasheet (.PDF)

