CrowdStrike Falcon Endpoint Protection Enterprise
Stop Breaches with Full Endpoint Protection
CrowdStrike Falcon Endpoint Protection Enterprise
Contact us for Pricing!
Get a Quote
CrowdStrike Falcon Endpoint Protection Enterprise sets the new standard in endpoint security with the first and only cloud-native security platform proven to stop breaches by unifying next-gen antivirus (NGAV), endpoint detection and response (EDR), managed threat hunting and integrated threat intelligence, in a single cloud-delivered agent.
Overview:
Unifies the technologies required to successfully stop breaches, including true next-gen antivirus and endpoint detection and response (EDR), managed threat hunting, and threat intelligence automation, delivered via a single lightweight agent.
Built to Stop Breaches
CrowdStrike Falcon Endpoint Protection Enterprise sets the new standard in endpoint security with the first and only cloud-native security platform proven to stop breaches by unifying next-gen antivirus (NGAV), endpoint detection and response (EDR), managed threat hunting and integrated threat intelligence, in a single cloud-delivered agent.
Key Benefits
- Stops breaches and simplifies endpoint protection
- Provides unparalleled realtime and historical visibility across endpoint events and activities
- Accelerates investigation and remediation and ensures stealthy attacks don’t go undetected 24/7
- Orchestrates and automates complex workflows with Falcon Fusion to simplify security operations and accelerate response
- Shows you the big picture with CrowdScore, your enterprise threat score
Cloud-Native Platform
- Reduces cost and complexity by eliminating the need for constant signature updates, on-premises management infrastructure and complex integrations
- Enables the industry's fastest deployment and rapid operationalization - without requiring a reboot after installation
- Only CrowdStrike provides full, automated protection across endpoints without impacting endpoint performance and end-user productivity
Business Value
![]()
Increases Security Efficiency
![]()
Improves Productivity
![]()
Decreases Risks of Breach
![]()
Reduces Time to Respond
Capabilities:
AI-Powered NGAV
- Protects against the entire attack spectrum
- Combines the best prevention technologies: machine learning, AI, indicators of attack (IOAs), exploit blocking and more, to stop known and unknown malware, ransomware, malware-free, fileless and sophisticated and stealthy nation-state attacks
- Fully protects endpoints both online and offline
Intelligent EDR
- Prevents silent failure by capturing raw events for automatic detection of malicious activity, providing unparalleled visibility, proactive threat hunting and forensic investigations
- Unravels an entire attack in one easy-to-grasp process tree enriched with context and threat intelligence data
- Provides powerful response action to contain, investigate and remediate compromised systems
24/7 Managed Threat Hunting
- An elite team of security experts proactively hunt, investigate and advise on activity in your environment to ensure threats and high-priority alerts don’t get missed
- Alert prioritization uniquely pinpoints the most urgent threats in your environment and resolves false positives
- Guided response provides clarity on an attack and guidance on what to do next
Device Control
- Provides detailed visibility on USB device usage
- Granular policy enforcement ensures control over USB devices being used in your environment
Firewall Management
- Makes it easy to create, manage and enforce policies
- Defends against network threats and provides instant visibility to enhance protection and inform action
Integrated Threat Intelligence
- Enables you to fully understand the threats in your environment and easily prioritize a response with threat severity assessment
- Eliminates guesswork, so you can respond to threats decisively
- Automatically determines the scope and impact of threats found in your environment
- Provides a broader set of indicators of compromise (IOCs) for faster, better protection
Modules Include:

Falcon Prevent
Next-gen AV
Protects against both malware and malware-free attacks; third-party tested and certified, allowing organizations to confidently replace their existing legacy AV

Falcon Insight
Endpoint Detection & Response
Delivers continuous and comprehensive endpoint visibility across detection, response and forensics, so nothing is missed and potential breaches can be stopped

Falcon X
Integrated Threat Intelligence
Integrates threat intelligence into endpoint protection, automating incident investigations and speeding breach response

Falcon Device Control
USB Device Protection
Enable safe and accountable USB device usage with effortless visibility and precise and granular control of USB device utilization

Falcon Overwatch
Threat Hunting Service
Identifies attacks and stops breaches 24/7 with an elite team of experts who proactively hunt, investigate and advise on threat activity in your environment

Falcon Firewall Management
Host Firewall Control
Provides simple, centralized firewall management, making it easy to manage and enforce host firewall policies
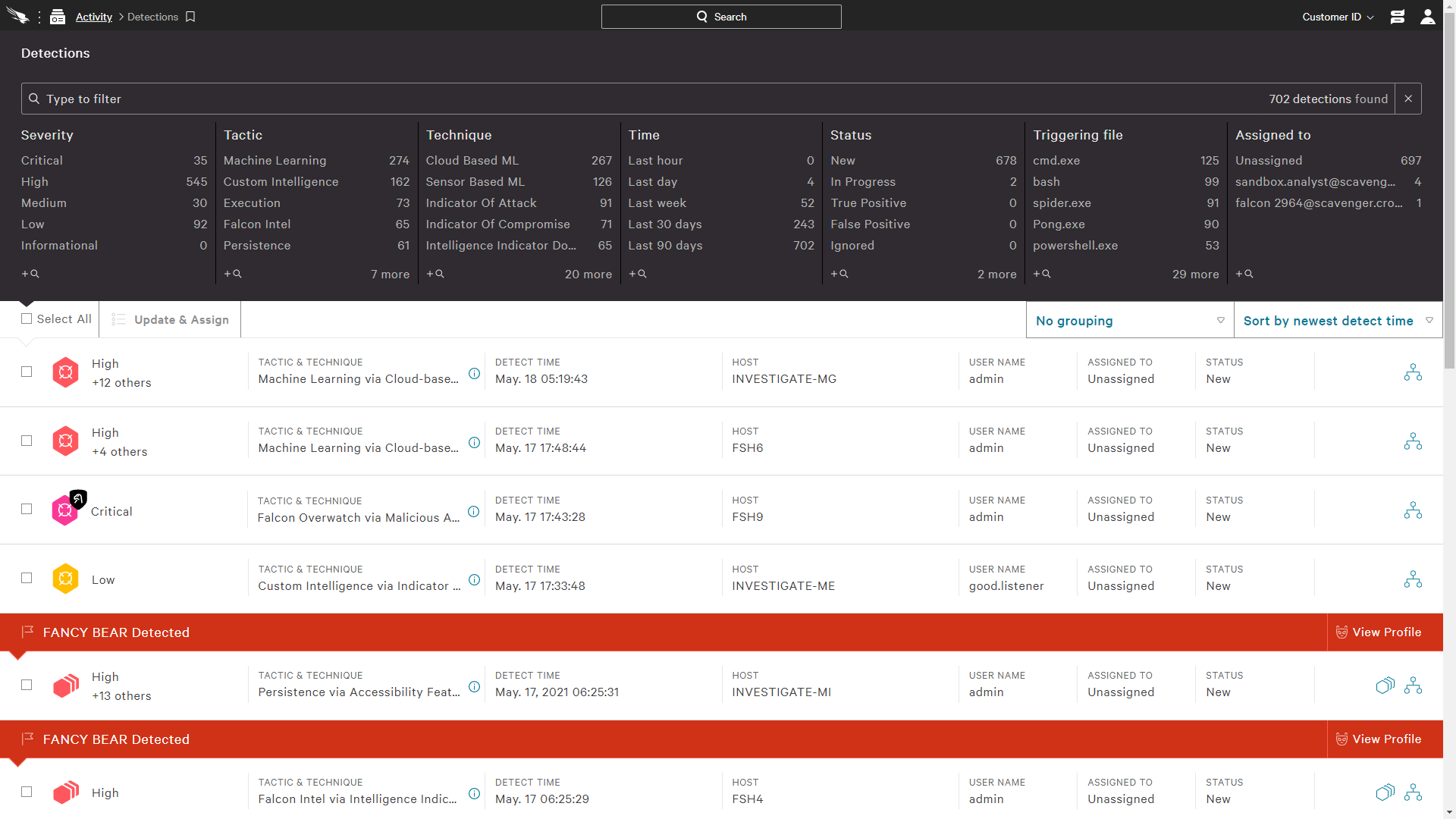
Screenshots:
Stop Breaches
Prevents and detects attacks beyond malware
- Unparalleled coverage defends against all types of attacks from malware to the most sophisticated and stealthy nation-state attacks
- Full EDR prevents silent failure by capturing raw events for complete visibility
- Speed investigations and act fast with intelligent prioritization and powerful Incident Workbench
- Continuous raw events capture empowers proactive threat hunting
- Threat intel integration and powerful real-time response capabilities speed up investigation and remediation and enable deep understanding of the attacks in your environment
- 24/7 managed threat hunting ensures stealthy attacks don't go undetected
The New Standard for Endpoint Protection
Intelligent EDR automatically detects attacks and threat intel integration provides attribution
- Falcon Endpoint Protection Enterprise offers a radical new approach to endpoint security by unifying the technology, intelligence and expertise needed to successfully stop breaches, in a single lightweight agent powered by Threat graph.
Simplify Endpoint Protection
Tens of thousands of endpoints operational in hours
- Deploys in minutes and is immediately operational
- Operates with only a tiny footprint on the endpoint
- Intelligent EDR and proactive threat hunters automatically detect attacks
- Integrated threat intelligence accelerates incident remediation
- Integrated Falcon Fusion orchestrates and automates complex and repetitive tasks - from notifications to response workflows
- Additional and new capabilities are delivered by the CrowdStrike Falcon platform without requiring any deployment
- Automatically kept up-to-date with SaaS delivery
- Adapts to all needs, growth and security status
- Simplifies operations with the Falcon agent and console managing both firewall capabilities and USB devices
See the Big Picture with CrowdScore
- CrowdScore provides a simple metric to help executives measure and understand the current threat level of the organization, and how it's changing over time.
- With CrowdScore, executives can make fast decisions and act to coordinate optimal response./li>
AI Powered NGAV
AI powered Machine Learning and IOAs protect against attacks
- Protects against known and unknown malware, and malware-free or fileless attacks
- Combines the best and latest prevention technologies such as machine learning, AI, indicators of attack (IOAs) and more
- Eliminates ransomware
- Covers the gaps left by legacy AV
- Fully protects endpoints online and offline
- Cleans up known artifacts left behind from blocked malicious activity
EDR
Intelligent EDR automatically detects attacks and threat intel integration provides attribution
- Continuous raw event recording provides unparalleled visibility
- Full endpoint activity details enable proactive and managed threat hunting and forensic investigations
- Intelligent EDR automatically detects malicious and attacker activity
- Unravels entire attack in one easy-to-grasp process tree enriched with context and threat intelligence data
- Provides powerful response action to contain and investigate compromised systems, including on-the-fly remote access to endpoints to take immediate action
Managed Threat Hunting
An additional layer of monitoring and analysis to ensure that threats never get missed
- Proactively hunts for threats 24/7, eliminating false negatives Uniquely pinpoints the most urgent threats in your environment and resolves false positives Threat hunters partner with your security operations team to provide clarity on an attack and guidance on what to do next.
Device Control
Detailed visibility on USB devices utilization
Reduces the risks associated with USB devices by providing:
- Granular policy enforcement to ensure control over USB devices used in the environment
- Effortless visibility across USB device usage, including what files are being copied to USB storage
- Insightful dashboards automatically provide detailed information such as class, vendor, product, serial number
Firewall Management
Host firewall management made easy
- Easily create, enforce and maintain firewall rules and policies
- Simplify operations by using the same lightweight Falcon agent, management console and cloud-native architecture
- Automatically identify and view specific activities, potential threats and network anomalies
Integrated Threat Intelligence
Fully understand the threats in your environment and what to do about them
Malware research and analysis at your fingertips:
- Eliminate guesswork and uncertainty to respond to threats decisively
- Automatically determine the scope and impact of threats found in your environment
- Easily prioritize responses with threat severity assessment
- Immediately get recovery steps and resolve incidents with in-depth threat analysis
- Find out if you are targeted, who is targeting you and how to prepare and get ahead
The Power of the Cloud
Tens of thousands of endpoints operational in hours
CrowdStrike's cloud-native platform eliminates complexity and simplifies endpoint security operations to drive down operational cost
- Reduced cost and complexity: Operates without the need for constant signature updates, on-premises management infrastructure or complex integrations.
- Protection of the crowd: Allows everyone to be protected against a threat encountered in just one environment. Automatically scales to adapt to growth and changing needs.
- Restores endpoint performance: Installation and day-to-day operations bear zero impact on endpoints - even when analyzing, searching and investigating.
- Works on day one: Deploys and is operational in minutes.
Compare Falcon Endpoint Protection Solutions:
Flexible Bundles:
![]() Included Component
Included Component
![]() Elective Component
Elective Component
Support:
CrowdStrike offers premium support services to assist you with deployment and ongoing use of the CrowdStrike Falcon platform to ensure your success in keeping your environment secure and stopping breaches.
The CrowdStrike support organization is dedicated to resolving any issues quickly and effectively
CrowdStrike provides multiple levels of support so you can choose the level that best fits your organization’s requirements and ensures that you receive the most benefit from your investment in CrowdStrike.
CrowdStrike provides four levels of support:
Standard Support
Standard Support is bundled free with all Falcon subscriptions, providing basic support services, with a next-business-day response service level agreement (SLA).
Express Support
Express Support is designed for customers in small to medium-sized enterprise environments where deployment and operational issues must be addressed as quickly as possible.
Express Support provides everything included in Standard Support, plus:
- Prioritized case handling
- Quarterly health checks and reports
- Knowledge transfer opportunities
- Access to CrowdStrike’s team of technical account managers (TAMs) for product advice and issue escalation
- Enhanced knowledge base
- Premium video and webinar content
Essential Support
Essential Support is designed for mid-sized enterprise environments. From planning your deployment to ongoing operations, CrowdStrike’s team of support professionals understands the importance of your mission and are committed to working with you to avoid problems and resolve issues as quickly as possible.
Companies that value proactive engagement to avoid issues and fast and predictable access to support will benefit from this service.
Essential Support provides everything included in Express Support, plus:
- 30 days of personalized onboarding support
- Invitations to Beta Programs
- Periodic proactive calls from a TAM
- Reports covering the overall health of your CrowdStrike deployment, best practices, tuning, case status and reviews of new product features and capabilities
Elite Support
Elite Support is the highest level of support provided by CrowdStrike. A named TAM works closely with you as an extension of your team.
Elite Support builds on CrowdStrike Essential Support and adds the following:
- Custom reporting
- Weekly scheduled meetings
- On-site visits (up to quarterly)
- Product management team access
- Named TAM
| Support Level | Standard | Express | Essential | Elite |
|---|---|---|---|---|
| Support Access | ||||
| Support Portal (Knowledge Base, Case Submissions) | ||||
| 24/7/365 Phone Support for Emergencies | ||||
| Live Chat (Business Hours) | ||||
| Priority Case Assignment | ||||
| Premium Support Content (Articles, Videos, Webinars) | ||||
| Access to TAM Team for Product Advice and Escalations | ||||
| Named TAM | ||||
| Technical Account Management | ||||
| Proactive Case Management | ||||
| Quarterly Reports | Custom | |||
| Weekly Deployment Follow-up Meetings | ||||
| Proactive Outreach | ||||
| Quarterly Health Checks | ||||
| Beta Program Invitations | ||||
| Roadmap Webinars | ||||
| On-site Visits | ||||
| Ad-hoc Product Guidance and Knowledge Transfer | ||||
| First 30 Days Ramp-Up | ||||
| Welcome Letter | ||||
| 1:1 Quick Start Call | ||||
| Weekly and Monthly Premium Support Newsletters | ||||
| Onboarding Webinar | ||||
Support Care
Response Time
- Standard: The support engineer responds to technical issues within one business day of a call or one business hour for critical issues.
- Express, Essential: The support engineer responds to technical issues within four business hours of a call or one business hour for critical issues.
- Elite: The support engineer responds to technical issues within four business hours of a call or one business hour for critical issues.
24x7 Critical Issue Support
- Standard: For critical technical issues (P1 - Network down), the support team is available around the clock.
- Express, Essential and Elite: For critical technical issues, the team will be available around the clock, escalating issues as appropriate for the quickest possible resolution. You will be given a dedicated phone number for these critical cases.
Prioritized Case Handling
- Express, Essential and Elite Support cases take precedence over Standard cases at the same priority level.
Proactive Support
- Essential and Elite: During periodic calls scheduled at your convenience, a member of the TAM team will provide Q&A or just-in-time training on topics of your choice, updates on the latest product features, and general platform health checks.
Product Care
Defect Handling
- Standard: When determined the issue could be caused by a defect in the product, a case will be opened on the customer’s behalf and managed to resolution.
- Express, Essential and Elite: When determined the issue could be caused by a defect in the product, the customer’s ticket will take precedence over others within the same priority level.
Feature Requests
Feature requests should be submitted through the Ideas section in the Falcon Support Portal where they are regularly reviewed and prioritized by the product teams.
Account Care
Technical Account Manager Team
- Express, Essential and Elite: You receive direct access to the TAM team, which will be your liaison to support and product management.
Documentation:
Download the CrowdStrike Falcon Endpoint Protection Enterprise Datasheet (.PDF)
Download the CrowdStrike Falcon Support Datasheet (.PDF)